As you will see, the story consists of three sections. The first section deals with malware, such as computer viruses, adware, etc. The second section looks at scams both online and by telephone. The third section deals with how to identify and avoid reposting fake or dishonest items on social media platforms such as Facebook and Twitter.
We will start by defining the term “malware.” If you are a wordsmith, you recognize the prefix, “mal” as meaning “bad,” so malware is bad software. In other words, it is software that is designed to cause some kind of harm to you or to some organization in which you are a member. Malware includes computer viruses, spyware, adware and scareware. Malware like computer worms, ransomware and Trojan Horses are types of computer viruses.
A computer virus consists of executable code (computer program), a script (which might be on a web page or word processing document) or active content from a web page. Ransomware encrypts all of the files on your hard drive, and then you are required to pay a fee to have it released. Hospitals, businesses and even law enforcement agencies have all fallen victim to ransomware attacks.
The three best things you can do to protect your data are to back up everything, to back up everything and to back up everything. Three ways to back up your important items are to use a cloud site, burn them to a CD or DVD or to use an external hard drive.
The three best things you can do to protect your data are to back up everything, to back up everything and to back up everything.
I use three different cloud sites so that I do not exceed the free storage space on any of them. Those are OneDrive, Dropbox and Google Drive. As a retired WLU faculty member, I have been able to keep my WLU email address that is hosted by Google. One of the perks is that WLU faculty members have a little more free storage space on Google drive as part of that relationship. You can also can sign up for a free Google account, which gives you 15 gigabytes of free Google Drive storage space. Obviously, that will fill up quickly if you save a lot of videos or high-resolution photos. The free version of OneDrive provides you with 5GB of online storage and the free version of Dropbox provides 2GB of online storage.
Another backup option is to burn your files to a CD or DVD. CD and DVD disks are inexpensive and easy to make, but they do not hold much data, so you might need a bunch of disks to back up all of your files. Today, I use DVD disks instead of CD disks because DVD disks hold more data.
The fastest way to back up everything on the hard drive of your laptop is to use an external hard drive. A one-terabyte external hard drive costs well under $100. A two-terabyte model will set you back just over $100. All you do to install the external hard drive is to plug it into a USB port and wait a few minutes for Windows to install the driver and tell you that it is ready to use. Then, you can simply create a folder on the external hard drive and drag the files and folders from your laptop into it to back them up. Be sure to back up your email and phone contacts if they are not already backed up somewhere else. You will also want to copy your Internet bookmarks and favorites and paste them into a Word document so that you can save them on your external hard drive. You can even use the backup and restore function in Windows to create a backup of your computer system on that external hard drive.
After I back up my files onto the external hard drive, then I remove it from the computer to prevent it from being infected if I should encounter a virus. How often you back up depends on your activity. You do not need to do a full backup very often, but you need to be sure to back up any new files that you have obtained or created since your last backup.

One of the other first things that you can do to avoid malware attacks is to make sure that you have a good antivirus program on your computer. If you are running Windows 10 on your computer, then Windows Defender Anti-Virus came preinstalled on your machine.
The good news is that Defender is actually pretty good at helping you avoid virus attacks. If you want a little more protection, you might opt for one of the other free antivirus programs. The two most popular free antivirus programs are Avast Antivirus with almost 420 million downloads and AVG Antivirus with over 566 million downloads. I have used both of them on different machines and can testify that they both work very well.
The bad news is that you can still fall victim to malware if you are not careful.
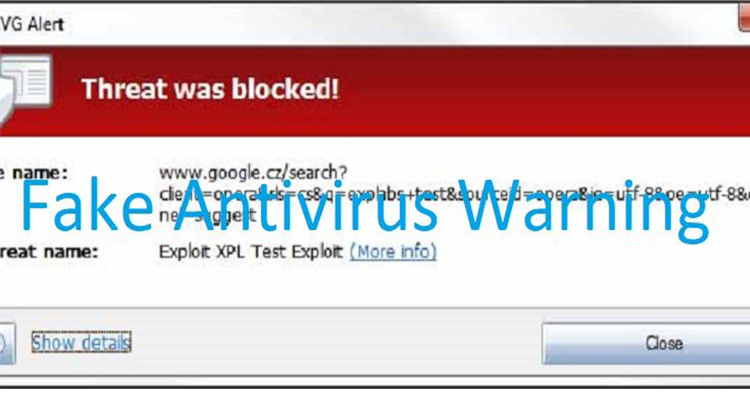
A couple of months ago, I was reading a news story on the website of a Cincinnati, Ohio, newspaper when a window popped up on my screen warning me that my computer was infected by a virus. The window appeared to be from Norton Anti-Virus. It had a button that said, “Click here for a full system scan. (Recommended).”
I immediately put my finger onto the power button on the laptop and held it down, thereby forcing my laptop to shut down. Then, I disconnected our wireless router to prevent the computer from automatically logging onto the Internet. After turning off our wireless Internet, I rebooted the laptop, which took several minutes because of the forced shutdown. After the system was up, I ran CCleaner, which is a free program that will remove all of the temporary system files and temporary Internet files.
When the pop-up window appeared, I had been using the Firefox Web browser, so I double clicked on it again. Sure enough, Firefox attempted to connect to a bogus web page instead of to my home page, so I clicked the home button to make it attempt to connect to Bing, which I have set as my home page. Because it was not online, it could not connect to Bing either, but I wanted to get it off of the virus page. Then, I erased the history file, closed the browser and reopened it to be sure that the default home page had not been reset. It had not. After closing the browser, I ran a full system scan using Windows Defender. It came up clean. Then, I reconnected the router and waited until it had connected to the Internet. After that, I again rebooted the laptop and opened Firefox to be sure everything was good.
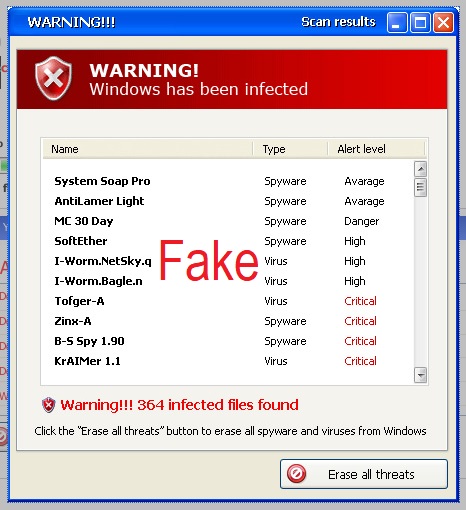
Bottom line: That popup box was an attempt to bait me into giving it permission to install malware onto my computer. If I had clicked the scan button, it would have likely installed a virus or ransomware onto my laptop. I am not using Norton anti-virus, but I would have known that box to be bogus even if I were. Never click on anything when that kind of box pops up. Follow the procedure outlined above instead. If it really is a warning from your antivirus program, it will still be there when you reboot offline and scan with your own antivirus program.
Another kind of malware is a PUP or “Potentially Unwanted Program.” If you are downloading and installing any free software, including the free antivirus programs, go slowly, and carefully look at every menu and at all of the check boxes on the screen. Many times, providers of free software will attempt to trick you into installing software that you do not want. When I installed CCleaner on my new laptop, I noticed a prechecked check box on a line that gave me the option of installing a Google toolbar. I had to uncheck that box to avoid installing that toolbar. With some software, the first download button to appear on the screen is for some other program instead of the one you are trying to download, so you need to be alert to be sure you are clicking the proper download button.
By the way, browser toolbars are not inert. Some of them track your online activity and communicate that information to advertisers, so they qualify as spyware or adware. Therefore, they are potentially unwanted programs (PUPS). If a site is trying to download a PUP onto your computer without your knowledge, your antivirus program will likely block it. If you click a download button for that PUP, then you have bypassed that antivirus program by giving permission for that PUP to be installed.
Malware does not all come from the web. Sometimes, it is distributed by users like you and me. That is especially true for Trojan Horse type malware. Consider this scenario: You get an email message from a good friend that says, “Check out this cute video.” Attached there is a document titled, “Mr. and Mrs. Santa.mpg.exe.” When you click on it, you see a cute and slightly risqué animated video of Mr. and Mrs. Santa, so you share it with your friends.
What you don’t realize is that by clicking on that video, you have installed malware onto your computer. That malware might be a virus or it might be adware or spyware. It might be Remote Access Technology (RAT) software that gives another person the ability to control your computer. It might be a keystroke logger that gives someone access to everything that you type, including your user names and passwords. Never click any email attachment that ends with .bat, .com, .exe, .pif, .cfg, .scr or .vbs. These are different types of program files. Notice that the above example that appeared in my WLU email several years ago ends with the .exe extension.
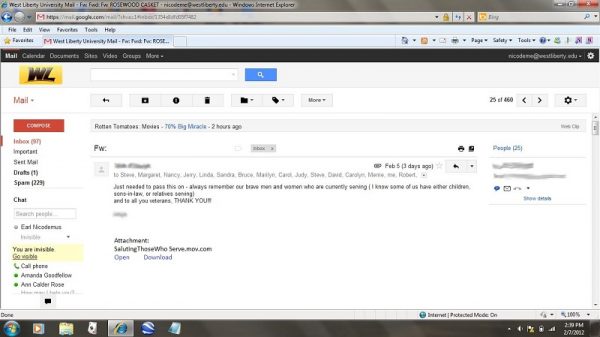
Email scammers are very clever. Phishing (pronounced fishing) is an attempt to bait you into giving a scammer your private information such as a credit card or bank account number, your social security number or your login information. The above screen capture is from an email that I received a few years ago. After a lot of thought, I decided that I had not ordered anything from Amazon and was about to click the link to cancel the order when I realized that it might be a phishing attempt.
So, I went to Amazon.com and logged onto my account. When I reviewed my order history, the item did not show up. I later learned that the scammers were using these bogus emails to trick people into giving them their Amazon login information and their credit card numbers.
A couple of years later, I received another phishing attempt that claimed to be from PayPal. Once again, they were trying to obtain my PayPal login information and my credit card number. If you receive an email like the one below, go to the company website and log onto your account instead of clicking any link in the email.
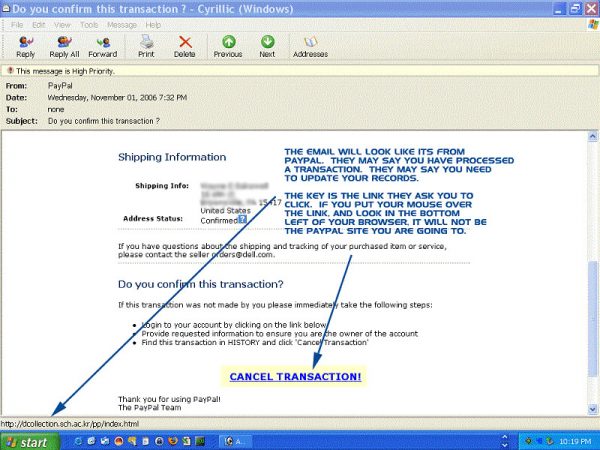
Phone scammers use some of the same tricks. The Medicare guy hung up on me. While Betty was outside, her phone rang, and I answered it even though it was an out-of-town number that I didn’t know. A guy with a thick accent asked for me. Without saying the word “yes,” I assured him that it was me and asked what I could do for him. He told me that he was calling from Medicare as a customer service representative. Then, he asked if I had received my red, white and blue Medicare card yet. I responded by asking where he was calling from. After a short delay, he said that he was calling from Pennsylvania.
I informed him that two of my fields of interest were cyber scams and phone scams. Then I told him that I would need the street address and city from which he was calling so that I could verify that he was actually from Medicare. The line went dead immediately. Don’t you think that it was rude for Medicare to hang up on me?
Last fall, the news reported on the fake IRS phone scam. People would get phone calls from the IRS informing them that illegal or improper activity was detected on their accounts and that they needed to pay overdue taxes or fines to keep from being arrested. Some of my Facebook friends mentioned that they had been called. However, that is not how the IRS operates. If they question something on your return, they send you a nice letter asking you to explain it by submitting a form and whatever documentation you wish. All of those threatening phone calls were bogus, and people paid thousands of dollars to those scammers. I suspect they also collected lots of social security numbers.
If someone calls you from a governmental agency, ask them for the street address and city where their office is located. If they are legitimate, they should already have your social security number. If they threaten to take legal action or to have you arrested, tell them to mail the information to you. If they are real, they will already have your mailing address.
By the way, I try to never say words like “Yes” or “Sure” or “OK” when talking to any telemarketer because there have been cases where scammers have recorded those words and then used an audio editor like Audacity to edit them into a phone conversation wherein they ask you if you want to sign up for a credit card or for some product or service. In the current version of this scam, the caller claims to be from Social Security. They tell you that your account has been compromised and ask you to verify your social security number. If you receive such a call, just hang up because it is a scam designed to get your social security number.
While we are thinking about phone scams, it is worthwhile to warn you about the one-ring robocall scam. The robocall rings your phone once and then hangs up. It may do this several times often in the middle of the night. Curious to know who was trying to reach you, you hit the “call back” button on your phone. However, you have taken the bait and fallen into the trap because the call-back number is actually a toll call number similar to a 900 number, and you are instantly charged with a heavy fee for your return call. That fee goes into the pocket of the scammer. The FCC advises us to NEVER return a call from an unknown number. Most of the current rash of “one ring and drop” calls are coming from the African nation of Mauritania.
Do you remember that old adage, “If it sounds too good to be true, it most likely isn’t true?” About 20 years ago, one of my friends received information in the mail about a drawing for a brand-new fishing boat complete with motor, so he filled out the entry form and sent it in. Some weeks later, he received another letter informing him that his number had been drawn and that he was the lucky winner of a brand-new boat and motor. The letter provided him with an address where he could stop by and pick up the boat and motor.
The only problem was that the address was in California. The letter included a number to call if he needed to arrange to have the boat and motor shipped to his location. He called the number and was informed that the shipping cost would be $250. If he chose to accept the price and have it shipped, he could submit the shipping form, which was enclosed with the letter informing him of his win, and pay the shipping by check or credit card. Figuring that $250 was cheap for a new fishing boat, he filled out the form, enclosed a $250 check and sent it to the contest officials. He soon received a letter informing him that the boat had been shipped. A couple of weeks later, two somewhat small packages arrived via UPS. One package contained a very small inflatable rubber boat, and the other contained a very small and inexpensive electric trolling motor. The total value of the two items was less than $50. However, he did receive a new boat and motor.
Scammers collect millions of dollars from Americans every year. The best overall advice is to never reply to an email or telephone call advising you that you have a problem. Instead, go to the agency referenced in the call or email and check on your account. Never click on a link in an email and never agree to anything from a phone call unless it is a call that you have made. Remember that immediate action is almost never required. If you have a problem with any governmental agency, they will notify you by letter and give you the opportunity to address the problem using their “due process” system.
As always, I invite your comments and additions to this article.